Our security partners
Consist's technology partnerships are characterized by a continuous transfer of know-how and many successful security projects at a high international level. Our partners are among the leading providers worldwide.
Consist IT Security
Within our security portfolio, we incorporate the market-leading security expertise of partner products in some areas.
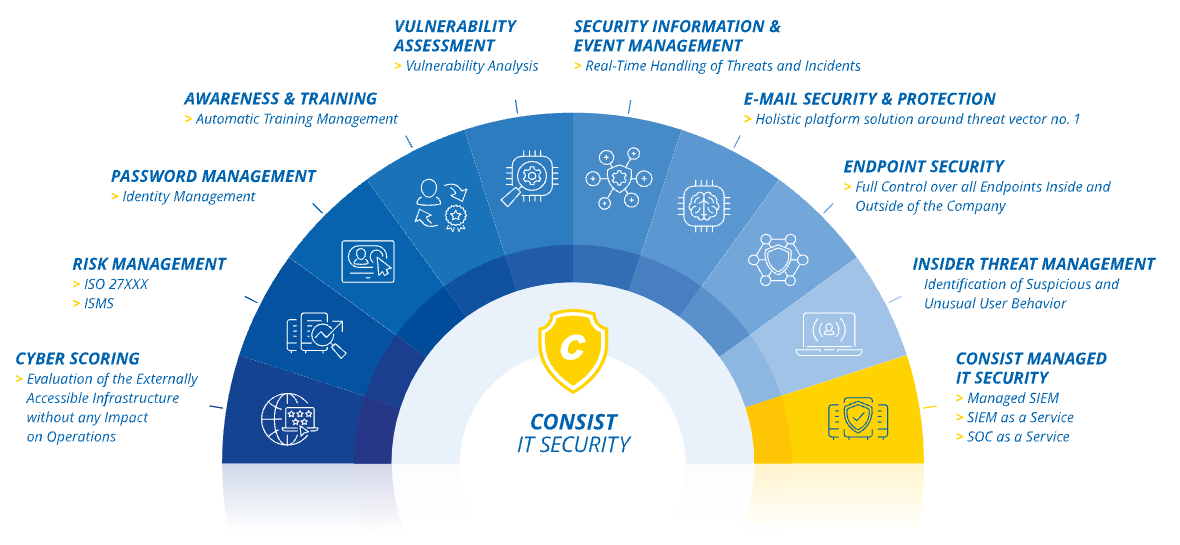
Security Information and Event Management - SIEM
> Splunk: data miracle and security engine in one
User experience monitoring
> uberAgent: security and optimization of application services
E-Mail Security
> Proofpoint - holistic E-Mail Security
Insider Threat Management
> ObserveIT | Proofpoint ITM - User Behavior Monitoring for external and internal Users
> Ekran System - extended platform solution for insider risk management
Awareness training
Syteca - Insider Risk Management
Management of Insider Threats throughout the whole cycle
In addition to all ITM functionalities from the area of access control, managing identities, detecting and reacting to insider threats, Syteca (formerly Ekran System) has the following additional features:
- Privileged User Access Management
- Microsoft Power BI integration
- Alerting and blocking of USB devices
- Mass storage device control
- Saving sessions in encrypted format (forensic)
User Access Management by MATESO - Netwrix
Mateso Password Safe - Netwrix Password Secure
End-to-end encryption can enable the highest level of security for managing identities, passwords and documents. The encryption procedure takes place exclusively and directly between the client and the server. This means that third parties have no chance of reading or manipulating encrypted data. At the end of 2022 Mateso was taken over by Netwrix.
Password Safe keeps data safely within the company, even when the staff are working from home.
We integrate IT security made in Germany for you, in accordance with the compliance guidelines:
- Individual password management solution for every employee from the admin (FullClient) via the key user (switch between Full and LightClient) to the end user (LightClient)
- Company-wide protection of passwords and secrets by simple integration with role-based access control (additional feature RBAC)
- Control remains with the user company: through E2EE encryption with over 100,000 iterations
- AD connection and other interfaces for use for the existing identity management or as direct access and credential provider
Have a look at the >Fact Sheet and >Data Sheet for further technical information.
Your contact

Joscha Sternadel
Sales Lead Products
phone: +49 431 3993-775
mobile: +49 162 2130358
e-mail: sternadel@consist.de










